MFA vs. Phishing-Resistant MFA: How to Strengthen Your Account Security
Did you know that 90% of successful cyberattacks start with phishing?
Multi-factor authentication (MFA) is meant to protect your accounts, but sometimes it isn’t enough. Even with MFA, attackers continue to find ways to bypass security measures through sophisticated phishing campaigns. That’s where phishing-resistant MFA comes into play. Strengthening MFA with phishing-resistant methods ensures that your users are protected even against the most advanced social engineering attacks.
Why Phishing-Resistant MFA Matters
MFA has improved account security across organizations, but not all MFA is created equal. Traditional methods, like SMS codes or authenticator apps, can still be intercepted or tricked by phishing attacks. Attackers exploit these vulnerabilities to gain unauthorized access, often without users even realizing it.
Understanding the Difference Between MFA & Phishing-Resistant MFA
Phishing-resistant MFA solves this problem by using authentication methods that cannot be easily stolen or replicated. Unlike standard MFA, which relies on something a user knows (like a password) or has (like a code), phishing-resistant methods tie authentication directly to the user’s device or cryptographic key. In phishing-resistant MFA, a private key is securely stored on the user's device and never transmitted to the server, ensuring that authentication remains resistant to interception. Modern authentication methods store cryptographic keys in secure hardware or software environments to prevent unauthorized access. This makes it virtually impossible for attackers to bypass, even if they manage to trick a user into revealing their credentials.
Adopting phishing-resistant MFA isn’t just about preventing hacks; it’s about strengthening trust, meeting compliance requirements, and protecting sensitive data from increasingly sophisticated threats. Passwordless MFA is a key feature of phishing-resistant authentication, eliminating the need for shared secrets. For organizations handling financial, healthcare, or other high-value data, it’s becoming a security essential rather than a nice-to-have.
Top Phishing-Resistant Methods to Strengthen MFA
Here are some of the most effective phishing-resistant authentication methods organizations can implement:
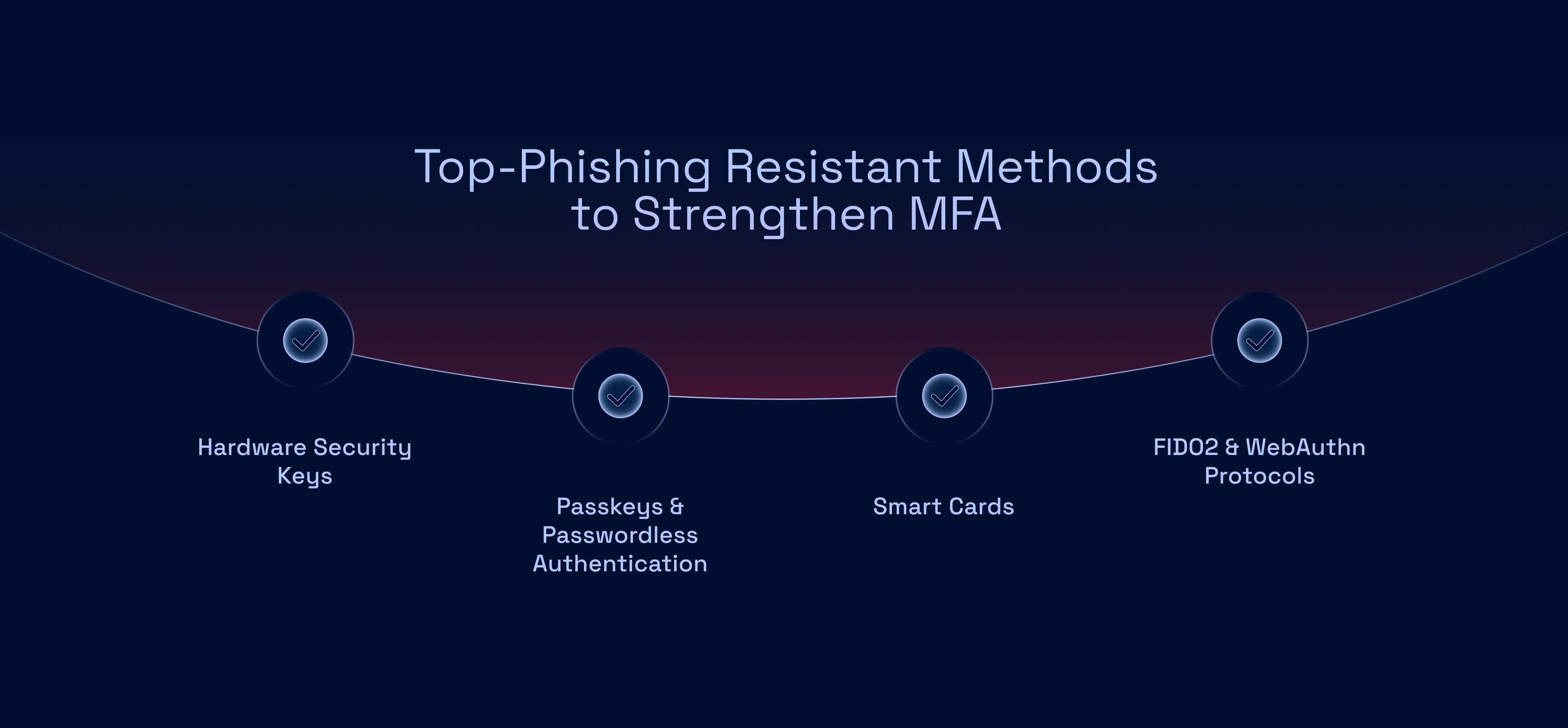
1. Hardware Security Keys
Hardware security keys, such as YubiKeys, are physical devices that users plug in or tap to authenticate. These keys require physical access to the device, making them resistant to remote attacks. Similar to an access card, a hardware security key requires tangible possession for authentication, ensuring that only authorized users can gain access. These keys store cryptographic credentials securely on the device, ensuring that login information never leaves the hardware. Because the authentication is tied to the physical key, attackers cannot remotely intercept credentials, making this method phishing-resistant.
2. Passkeys & Passwordless Authentication
Passkeys replace traditional passwords with cryptographic key pairs. Stored securely on devices, passkeys enable users to log in using biometric verification (like Face ID or fingerprint) or a device PIN. This method eliminates the risk of password phishing entirely.
3. Smart Cards
Smart cards function similarly to hardware keys but often integrate with enterprise systems like Active Directory. Federal agencies often require the use of smart cards for secure authentication in compliance with government cybersecurity directives. They store private cryptographic keys on the card itself and require a PIN for authentication, making unauthorized access extremely difficult. Smart cards are also effective in preventing attackers from gaining initial access to critical systems.
4. FIDO2 & WebAuthn Protocols
FIDO2 and WebAuthn are recognized as a global authentication standard developed by the FIDO Alliance, enabling phishing-resistant logins across web applications. These protocols define how devices—whether hardware keys, built-in device authenticators, or mobile devices—can securely authenticate users using public-key cryptography.
FIDO authentication is specifically designed to resist phishing and brute force attacks, providing stronger security unlike regular MFA methods that rely on vulnerable factors such as SMS or OTP. The FIDO Alliance is responsible for creating these open standards, ensuring that credentials cannot be phished, regardless of the device used.
MFA Best Practices
Even the most advanced phishing-resistant methods are most effective when paired with strong policies and user habits. Key best practices include:
- Enforcing MFA for all privileged accounts
- Encouraging passwordless logins where possible
- Regularly reviewing and updating MFA policies
- Training users to recognize phishing attempts

Implementing Phishing-Resistant MFA in Your Organization
Adopting phishing-resistant methods may require investment in hardware or software solutions, but the payoff in security is substantial. Start by identifying the most sensitive accounts and systems in your organization, then implement hardware keys, passkeys, or smart cards for these accounts. Pair these methods with employee education to maximize protection.
Educating Employees on MFA Security
Technology alone won’t stop phishing attacks. Employee awareness is just as important. Effective education focuses on building habits and skills that complement phishing-resistant MFA. Examples include:
- Phishing Awareness Training: Teach employees to spot phishing emails, fake login pages, and suspicious links using real-world examples.
- Simulated Phishing Tests: Periodically test awareness by sending mock phishing emails and providing immediate feedback.
- MFA Usage Guidelines: Show step-by-step procedures for using hardware keys, passkeys, and smart cards.
- Reporting Procedures: Make sure employees know how and where to report suspicious activity or unusual login prompts.
- Regular Security Refreshers: Offer short, recurring sessions or newsletters covering phishing tactics and cybersecurity best practices.
- Promoting a Security-First Culture: Encourage staff to treat security as part of their daily workflow and recognize proactive behavior.
By combining phishing-resistant MFA with ongoing employee education, organizations can create a robust, layered defense that protects both accounts and sensitive data.
Invest in Strong Authentication Methods for a Safer Digital Environment
The evolution of MFA toward phishing-resistant methods represents a major step in cybersecurity. By prioritizing phishing-resistant authentication, organizations are protecting sensitive data, strengthening compliance, and staying ahead of increasingly sophisticated attacks.
At Red Sentry, we help organizations understand emerging cybersecurity threats and implement strategies to mitigate risk. By sharing insights on phishing-resistant MFA and other strong authentication methods, we empower teams to protect sensitive data, stay compliant, and defend against increasingly sophisticated attacks.

.jpg)